9. DNS and DNS attack
DNS Hierarchy, Zones, and Servers
DNS Domain Hierarchy
Domain namespace is organized in a hierarchical tree-like structure
- Each node is called a domain OR subdomain when referencing to parent
- The root of the domain is called ROOT, denoted as '.'
Below ROOT, we have Top-Level Domain(TLD)_ex. In www.example.com, the TLD is .com.
The next level of domain hierarchy is second-level domain which are usually assigned to specific entities such as companies, schools etc.
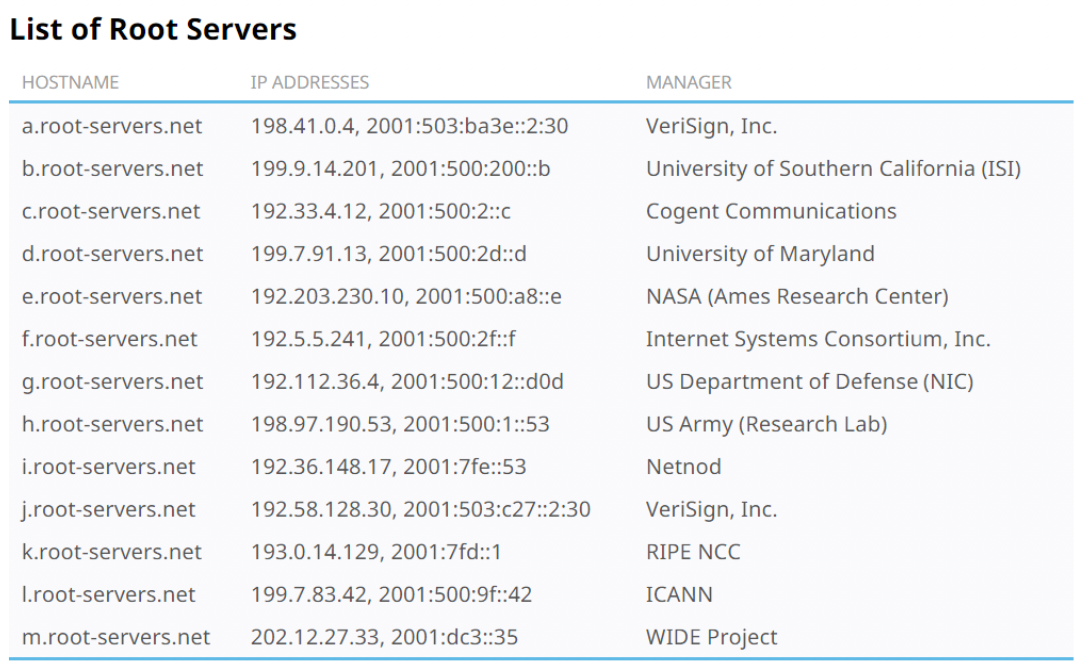
DNS ROOT Servers
The root zone is calle ROOT
- There are 13 authoritative nameservers (DNS root servers) for this zone.
There provide the nameserver information about all TLDs(about 2MB)
There are the starting point of DNS queries
Root servers are the most critical infrastructure on the Internet
Top Level Domain(TLD)
The official list of all top-level domains is maintained by the Internet Assigned Numbers Authority(IANA), which also oversees the approval process for new proposed top-level domains.
- Infrastructure TLD: .arpa
- Generic TLD(gTLD): .com, .net
- Sponsored TLD(sTLD): proposed and sponsored by private agencies/orgs to use the TLD:. edu, .gov, .mil, .travel, .jobs
- Country Code TLD(ccTLD): au(Australia), .cn(China), .fr(France)
- Reserved TLD: .example, .test, .localhost, .invalid
.(루트) ->
[1단계] 국가코드최상위도메인 -> .kr/ .jp/ .cn/ .한국 -> [2단계] 희망문자열선택(ex. domain.kr) -> [3단계] 희망문자열선택(ex. samsung.co.kr)
[1단계] 일반최상위도메인 -> .net/ .com/ .biz -> [2단계] 희망문자열선택(ex. naver.com)
Each TLD is delegated by IANA to a "designated manager", called registry
- There are strict protocols and policies that govern the selection of designated managers [Postel, 1994]
https://www.iana.org/domains/root/db/kr.html
.kr Domain Delegation Data
e.dns.kr 202.30.124.1002001:dcc:5:0:0:0:0:100
www.iana.org
한국인터넷정보센터(KRNIC)
도메인 소개, 등록 및 사용, IP주소, AS번호, DNS 정보, 관련규정 제공
xn--3e0bx5euxnjje69i70af08bea817g.xn--3e0b707e
인터넷주소자원에 관한 법률(약칭: 인터넷주소법)
등록대행자
인터넷진흥원(KISA)은 이용자에게 합리적 가격 및 다양한 부가 서비스를 제공하기 위해 경쟁체계 도입
이러한 국가 도메인 등록 업무를 진행하는 도메인 업체는 등록대행자이며, 등록대행자는 인터넷주소자원에 관한 법률에 근거하여 한국인터넷진흥원과 등록대행계약을 맺은 업체
DNS Zone
DNS is organized according to zones(도메인 영역)
- The domain hierarchty tree structure describes how the domain namespace is organized, but that is not exactly how the domain systems are organized
A DNS zone basically groups contiguous domains and subdomains on the domain tree and assign management authority to and entity
- Each zone is managed by an authority, while a domain does not indicate any authority information
- A domain can be managed by multiple authorities(i.e., divided into multiple zones)
The tree structure depicts subdomains within example.com domian
- 각 나라에 대해 하나씩 여러 DNS 영역 존재
- 각 subdomain에 대해 authority가 누구에게 있는지 기록 유지
- example.com을 위한 영역은 mail.example.com과 같은 subdomain에 속하지 X DNS record만 포함
- 회사는 domain과 subdomain을 모두 중앙의 entity 하나 ~> 관리 가능, 영역 하나만 생성_다른 국가 간의 종속성 문제 -> 바람직 X
- 각 국가의 지점간 독립성 유지 -> 회사는 subdomain 관리를 delegate(위임) -> 각국이 자신의 DNS 정보 관리
Zone vs. Domain
A DNS zone only contains a portion of the DNS data for a domain.
- If a domain is not divided into subdomains, the zone and domain are the same, because the zone contains all the DNS data for the domain.
When a domain is divided into subdomains, ther DNS data can still be put in the same zone, so doamin and zone are still the same. But, subdomains can have their own zones.
Authoritative Name Servers
Each DNS zone has at least one authoritative nameserver that publishes information about the zone.
- It provides the original and definitive answers to DNS queries.
An authoritative name server can be a master server(primary) or slave server(secondary).
- A master sercer stores the master copies of all zone records whereas a salve uses an automatic updating mechanism to maintain an identical copy of the master records.
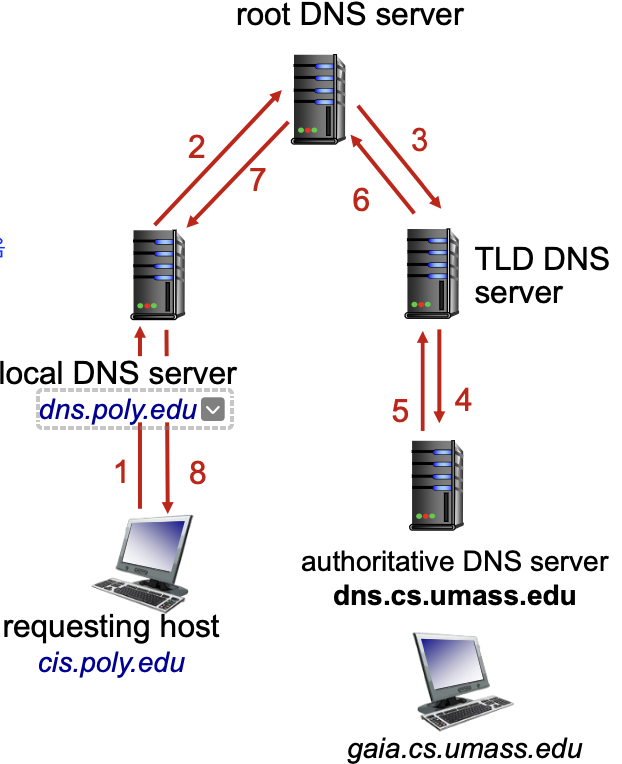
DNS Query Process
DNS Query Process
The applicaiton asks the DNS resolver on the local machine for the IP address
ㄴThe reslover first tries to find the IP address from its own data, and if failed, it will send a request to its helper(= local DNS server)
- ex. you can use 1.1.1.1 (Cloudflare) OR 8.8.8.8 (Google) DNS servers
- More clearly, the default DNS server instead local is rather correct.
Local DNS Files
/etc/host: stores IP address for some hostnames. Before machine contacts the local DNS servers, it first looks into file for the IP address.
127.0.0.1 localhost
127.0.0.1 www.CSRFLabAttacker.com
127.0.0.1 www.CSRFLabElgg.com
127.0.0.1 www.XSSLaabElgg.com
/etc/resolv.conf: provide information to the machine's DNS resolver about the IP address of the local DNS server. The IP address of the local DNS server provided by DHCP is also stored here.
Local DNS Server and Iterative Query Process
The iterative process starts from the ROOT Server. If it doesn't know the IP address, it sends back the IP address of the nameservers of the next level server (.NET server) and then the last level server (example.net) which provides the answer.

DNS Resolvers
Recursive DNS Resolver, Again
- In this all-DNS servers allow recursice query
- dig (+recurse) www.example.com
Iterative DNS Resolver
- dig +norecurse www.example.com
- dig +trace www.example.com
Emulating Local DNS Server(Step 1: Ask ROOT)

DNS Response

Steps 2-3: Ask. net & example.net servers

DNS cache
When the local DNS server gets information from other DNS servers, it caches the information.
Each piece of information in the cache has a time-to-live (TTL) value, so it will be eventually time out and removed from the cache.
Set Up DNS Server and Experiment Environment
We will use this setup for our experiment
- We will run these three virtual machines on one physical machine
- For the VM network setting, if you are using VirtualBox, please use "NAT Network" as the network adapter for each VM. If you are using Vmware, the default "NAT" setting is good enough.
Setup: User Machine
Setup: Configure Local DNS Server
Configure Local DNS Sercer: Simplification
Set Up DNS Zones on Local DNS Server
Zone File for Forward Lookup
Testing Our Setup
DNS Attacks
DNS Attacks
Overview of the Attack Surfaces
DNS Attacks on compromised Machines
Local DNS Cache Poisoning Attack
Spoofing DNS Replies(from LAN)
Local DNS Cache Posioning Attack
Inspect the Cache
Remote DNS Cache Poisoning Attack
Challenges
The Kaminsky Attack
The Kaminsky Attack: A Sample Response
Spoofing Replies: IP and UDP headers
Spoofing Replies: DNS Header and Payload
Attacks from Malicious DNS Server
Attacks from Malicious DNS Server
Fake Data in the Additional Section
Fake Data in the Authority Section
Reply Forgery Attacks from Malicious DNS Servers
Reply Forgery in Reverse DNS Lookup
Reply Forgery Attacks from Malicious DNS Servers
Reverse DNS Lookup
Reply Forgery Attacks from Malicious DNS Servers
Review Our Question
Protection Against DNS Cache Poisoning Attacks
Protection Against DNS Cache Poisoning Attacks
Protection Using DNSSEC
Protection Using TLS/SSL
Transport Layer Security (TLS/SSL) protocol provides a solution against the cache poisoning attacks.
- After getting the IP address for a domain name (www.example.net) using DNS protocol, a computer will ask the owner (server) of the IP address to proof that it is indeed www.example.net.
- The server has to present a public-key certificate signed by a trusted entity and demonstrates that it knows the corresponding private key associated with www.example.net (i.e., it is the owner of the certificate).
- HTTPS is built on top of TLS/SSL. It defeats DNS cache poisoning attacks
DNSSEC versus TLS/SSL
Both DNSSEC and TLS/SSL are based on the public key technology, but their chains of trust are different.
- DNSSEC provides chain of trust using DNS zone hierarchy, so nameservers in the parent zones vouch for those in the child zones.
- TLS/SSL relies on Public Key Infrastructure (PKI) which contains Certificate Authorities (CA) vouching for other computers.
DNS Rebinding Attack
Same Origin Policy (SOP)
Web browsers enforce a sandbox policy on AJax (Async. Javascript & XML), which only allows Ajax code inside a web page to interact with the same server where the page comes from
Rebinding Defenses
Browser Mitigations: Refuse to switch IPs mid session
- Interacts poorly with proxies, VPNs, CDNs, etc
- Not consistently implemented in any browser
Server Defenses
- Check Host header for unrecognized domains.
- Authenticate users with something else beyond IP address
Denial of Service Attacks on DNS
Denial of Service Attacks on Root Servers
Attacks on the Root and TLD Servers:
Root nameservers: If the attackters can bring down the servers of the root zone, they can bring down the entire Internet. However, attack root servers is difficult:
- The root nameservers are highly distributed. Ther are 13 (A, B, ... , M) root nameservers (server farm) consisting of a large number of redundant computers to provide reliable services.
- As the nameservers for the TLDs are usually cached in the local DNS servers, the root servers need not be queried till the cache expires (48 hrs). Attacks on the root servers must last long to see a significant effect.
Denial of Service Attacks on TLD Servers
Nameservers for the TLDs are easier to attack. TLDs such as gov, com, net, etc. have quite resilient infrastructure against DOS attack. But certain obscure TLDs like country-code TLDs do not have sufficient infrastructure.
=> The attackers can bring down the Internet of targeted country.
Attacks on Nameservers of a Particular Domain
UltraDNS
DNS provider for many major e-commerce companies such as Amazon, Walmart, Expedia. In 2004, DOS against this provider was launched which suffered an outage for an hour.
DNSPod
In 2009, serveral DNS servers of a Chinese domain service provider were hit by DDoS.
- The attack was meant to target one particular company (Baofeng.com) which is widely popular video streaming site in China.
- On the next day of attack, when DNS responses previously cached by the other servers timed out, Baofeng's media player on user's machines could not find the IP addresses of the servers because of the attack.
- Due to the bug in the media player software, instead of waiting, they continuously sent out DNS queries at a faster rate. Due to massive number of DNS queries, they flooded and congested the network of China Telecom (ISP). It impacted 20 provinces and is described as the worst Inernet incident in China.
Dyn network
In 2016, multiple DDoS attack were launched against a major DNS service provider for companies like CNN, BBC, HBO, PayPal etc. The attacks are believed to have been launched through botnet consisting of different IoT devices lice IP cameras, baby monitors etc. It caused major Internet services unavailable.
Summary
- How DNS works
- Spoofing Attacks on DNS
- Local DNS cache posioning attacks
- Remote DNS cache poisoning attacks
- Reply forgery attacks
- Defense against DNS spoofing attacks
- DNSSEC
- TLS/SSL
- Denial of Services on DNS
'📓 > 네트워크' 카테고리의 다른 글
| [Network Security] Attacks on the TCP protocol (0) | 2022.11.19 |
|---|---|
| [Network Security] Sniffing and Spoofing Part 1 (0) | 2022.10.22 |
| [TCP/IP Networks] 8. TCP Connection Establishment and Termination (0) | 2022.10.06 |
| [TCP/IP Networks] 7. TCP: Transmission Control Protocol (0) | 2022.10.01 |
| [TCP/IP Networks] 6. UDP: User Datagram Protocol (0) | 2022.10.01 |
